Technology Expert Witness Services
- Our firm has been operating since 1986
- Our Scientists and Analysts have more than 100 years of collective experience in their respective fields.
- More than 110 cases in state and federal courts.
- More than 40 testimonies.
- Ask us about our 10-figure courtroom victory.
Unlike most expert witness firms, we also create powerful courtroom presentations, including forensically accurate video re-creations of events. We have decades of experience presenting complex information in simple and accessible ways to audiences ranging from local juries of all levels of sophistication to the Pentagon, both Houses of Congress, 35 state and local regulatory bodies, and radio and national TV audiences, including Anderson Cooper 360.
We are proud and honored to serve on the approved Panel of Expert Witnesses for the Superior Court of the County of Los Angeles, California.
SERVICE AREAS
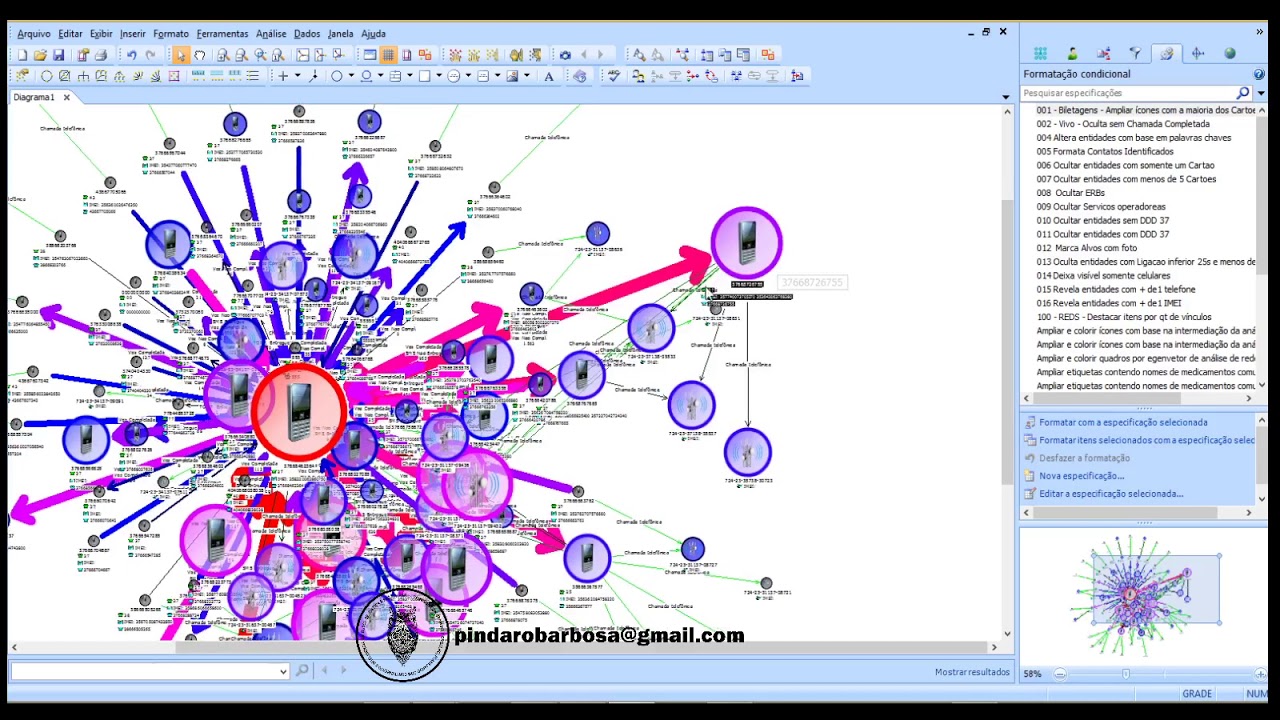
Cell phones store stunning amounts of evidence. If you don’t take advantage of that evidence, you may rest assured your Opposing Counsel will. But like traditional mystery stories, they do not “give up their secrets” easily.
Our firm uses multiple software tools to extract and analyze available data, often combining it with data from cell phone provider records and Internet Service Provider records as well.
GPS records are often vital to critical evidence. While a primary source of GPS data is cell phones, such data is also stored in computers, automotive Event Data Recorders and independent GPS systems, telephone company records, and digital photos, as well as many others.
Our firm is equipped to examine, analyze, and interpret GPS data of value to a case from many sources, and we have assisted numerous clients in this way.
Email records are often key evidence in court cases. Email evidence requires retrieval, including retrieval of deleted emails, authentication, and analysis. Often, analysis requires coordination with both the email provider and also the phone company or Internet Service Provider. It may be necessary to retrieve emails from mobile devices or computers as well.
We’ve been working with email cases for many years. Yes, we can help!
Don’t hesitate – the call is free!
Text messages have been a part of the communications landscape for a long time… since 1992. They often contain crucial evidence. But retrieving them can be difficult, since retention policies vary from provider to provider. As with so many other digital evidence channels, the use of text message evidence may require retrieving them from a mobile device or a computer and may required coordination with both the phone service provider and the internet Service Provider.
We’ve been working with email cases for many years. Yes, we can help!
Don’t hesitate – the call is free!
Social media started off as a way to chat with friends.
Who knew it would be used as a tool for human trafficking, money laundering, extortion, warfare, and disinformation?
We share your concern. Every single one of these cases is unique. If you have one of these cases on your desk, let’s talk.
A dear friend of ours, a 15-year veteran homicide investigator, once observed “You know, when I was a rookie cop, it was all about expended shell casings and fingerprints. Now, it’s all about storage media!”
Computers, devices, and storage media are the dominant force on the evidence landscape today. And they require loving care as much as any evidence in history.
DO NOT EVEN THINK of looking at an evidence drive yourself. That would be like carrying DNA evidence around in your lunchbox! By the same token, if a drive reports dead, don’t be alarmed. That’s normally due to a bad stepper motor on the internal arm, not a genuine loss of data… we can generally recover the data. And just because a file isn’t there anymore, that doesn’t necessarily mean it’s lost.
Every new technology is a new place to contribute to the USA’s ONE TRILLION DOLLAR FRAUD INDUSTRY. From backdated files to counterfeit PDFs to faked invoices to more other items than either of us can count, fraud goes with computers like Bonnie went with Clyde.
We’ve worked with our share of fraud, from inflated lawnmower wholesale invoices to church salary fraud to counterfeit DVDs
Both of our principals rebuilt engines as teenagers. Back then, there were manual chokes, you could tune your car with two screwdrivers, and you got about 12 MPG.
One of us, Robert, spent the next 43 years operating a 14-person auto repair firm, served on California state automotive boards and commissions, and has virtually every diagnostic license there is.
Many people are not aware that a modern car has MULTIPLE computers inside, including specialized ones for the seat belts and air bags, for a total of more compute power in a single car than the first moon landings. Reading those records is a bit like decoding the Rosetta Stone. But the results of doing so – and integrating the results with maintenance records, vehicle inspections, and, yes, possibly cell phone records, can make the difference in court.
If you thought all there was to a security camera was pushing a few buttons and exporting data to a thumb drive, think again.
Those files you can’t find? They might actually still be there. What if the system is damaged? We can probably still get the data. Is your statement good enough to withstand withering questions from Opposing Counsel? Hmmm.
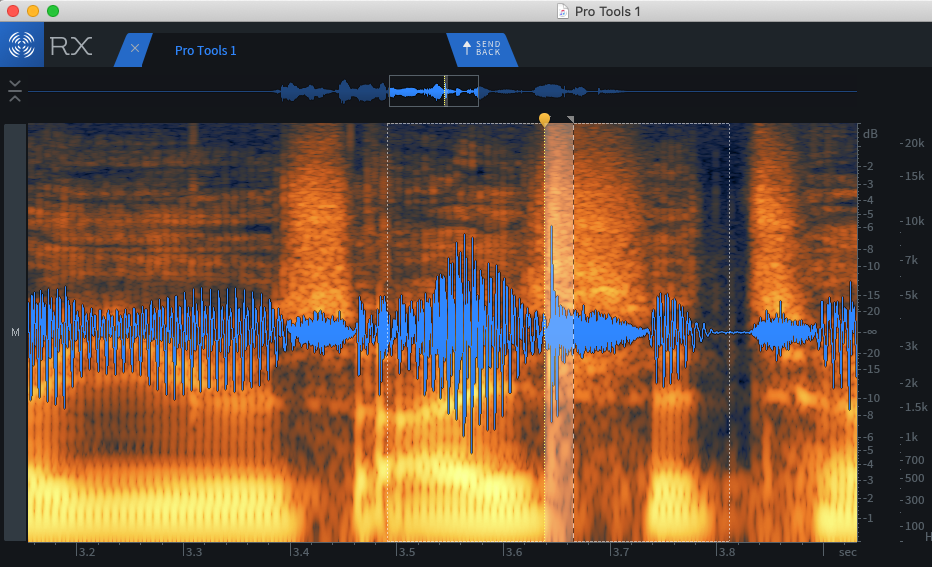
Who REALLY was that on the video? Was that the actual person you think it was, or was it an imposter? Can we make this voice recording more clear?
We do spectral, image analysis, and AI analysis of video and audio records!
Many people are surprised to discover that – buried within a photo itself – is a host of valuable information ranging from the GPS coordinates at the time the snap was taken to the lens type and focal length. Or, it might be fake. If that’s important to your case…
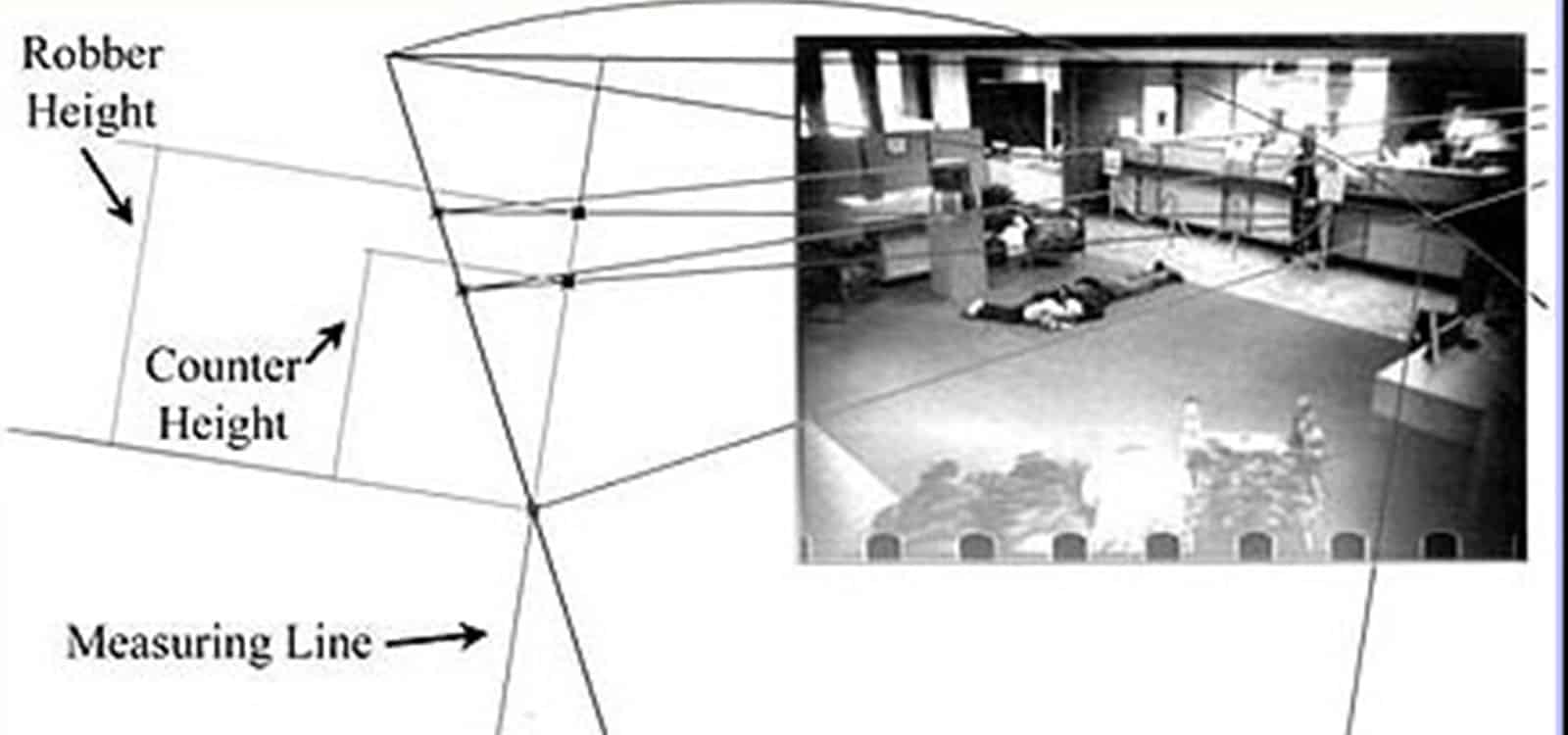
Little things mean a lot. For example, if the elevator car came to rest MORE than 1/2 inch from the floor when the woman tripped and fell and sustained life altering injuries, the award would be MUCH larger. But how do you compute that from a surveillance video when physical access to the elevator is denied? Ask us… we’d love to tell you. Or ask about the construction site accident resulting from improper berms where the photo evidence was, to put it mildly, amateurish. Or – was that vehicle in the accident REALLY part of a large firm’s national fleet, or was it just a close look-alike?
In any case involving complex movement [a “kinetic” case], where any part of the movement is in question, there is no finer method to fully explain to a jury what happened than to create an animation of the event. Known as “Forensic Videos”, these typically 10-second videos depict such things as injury details, automobile trajectories, gunshot wounds, public transit accidents, slip-and-fall dynamics, and related items. They are done to the highest standards of accuracy and impartiality. And the costs are surprisingly reasonable.
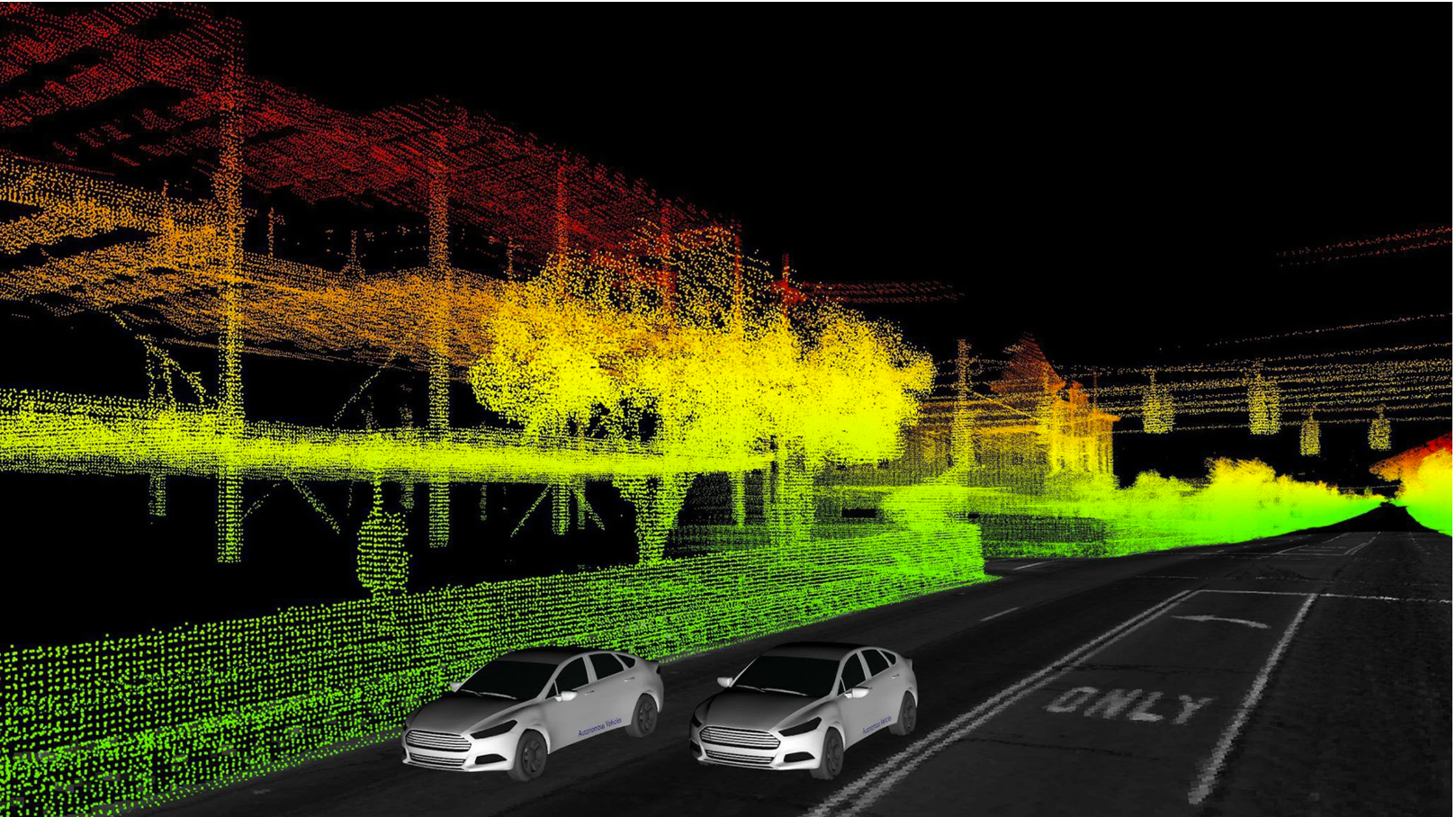
An acronym for Light Detection And Ranging, LiDAR is a technology for creating a “point cloud” of 3 dimensional measurements that can capture a 3D image of a scene, ranging from an accident to a building, with typically 1 millimeter accuracy and billions of points. It’s widely and successfully used in the process of evidence collection and display. We’d love to discuss it with you!
Flying can make you feel as free as a bird, but, hey, stuff happens to birds and people alike. In his salad years, our Principal Scientist, Wayne, was the owner of a Cessna Aircraft dealership, an aircraft Fixed Base Operation [”FBO”], and the Chief Pilot of a charter airline operating under Federal Aviation Regulation Part 135. An airline transport rated pilot and former flight instructor, he graduated 35 students for a range of licenses. He’s contributed to cases involving aircraft appraisals, pilot error, and aircraft operations.
Both Wayne and Robert have owned businesses for a collective total of more than 80 years.
Robert owned an automotive repair firm for 43 years prior to selling it to a Fortune 500 company.
Wayne is a serial entrepreneur who has owned a small airline, a restaurant, and a consulting firm. A trained accountant, he served as the President and CFO of a Ukrainian-American software firm he took public before the US SEC in 2005. He also served as the Vice President of an aircraft flight simulator company and as the Chief Scientist of a nuclear counterterrorism research laboratory that won several million-dollar contracts from the US House Armed Services Committee and the Joint Improvised Explosive Device Defeat Organization. [JIEDDO]. He is also a former contract Project Management instructor for several customers, including the US Navy.
In a word, we’ve got you covered for business analysis and valuations.
We can help you!
Wayne holds seven granted patents, six provisionals, and has authored two others, in the areas of neutron and gamma ray physics, less-than-lethal pistol ammunition, financial technology, real estate office processes, and remote identification of mobile lottery purchasers. He has also advised inventors on jam-resistant CAN bus architecture for military vehicles.
We can help you!
Wayne has performed both validation and valuation analyses for 8 related software patent cases in the courts of several states and also US Federal District Court in Denver, as one of the first two experts to testify in a long running case with 400 defendants. He cited as authorities IRS publications, AICPA SOPs, and AVA procedures, using both comparable sales, cost-to-construct, and related costing algorithms.
We can help you!
Human Terrain Mapping [“HTM”] is a Directed-Graph based presentation modality for creating network images of complex human situations, typically involved in areas such as criminal and civil securities and insurance fraud, money laundering, human trafficking, the narcotics trade, weapons sales, and terrorism.
Wayne was one of the first software developers of an early system, CNA [”Criminal Network Analysis”], which was used by the National Counterterrorism Center to track the movements of mastermind Timothy McVeigh, and by the FBI to solve what at the time was the US’s largest insurance fraud case and also the US’s largest stolen car ring. Wayne acted as the support engineer for the FBI. He later used the current best of breed HTM software, IBM’s i2 Analysts’ Notebook, in a complex murder conspiracy case in California.
FAQs
GLAD YOU ASKED! Computers store a lot of information you don’t see. That information is called “Metadata”, which means “Data about data”. The easiest way to think of metadata is to consider a normal book, with a title page, the name of the author, the publisher, the table of contents, and the chapter and page numbers. Those are all examples of metadata. Only the contents of the book is actually “data”. The metadata helps you understand items about the book, but it’s not the actual book.
In any legal scenario, the metadata can be as valuable – if not more valuable – than the actual data itself. And even the simple process of starting a computer that contains a drive about which there are questions, or of viewing a file, introduces new metadata. If the computer or its drive are evidence, that’s the equivalent of handling a piece of DNA evidence without gloves!
Computer forensic specialists like us and our colleagues create a bit-by-bit copy of the untouched evidence drive by connecting the evidence drive, powered down, to a forensic copying device certified by the FBI, NIST, or the Department of Justice as electronically unable to make changes to the evidence drive. The forensic copier then creates that identical copy on a new, blank drive.
At our lab, we refer to that first copy as a “Golden Master”, borrowing a term from the software industry. We also go one step further. We next make a second forensic copy of the Golden Master forensic copy, which we refer to as a “Working Copy”. We store the Golden Master securely. Its only purpose going forward would be to generate additional Working Copies.
We perform all our analysis on Working Copies.
A “Digital Fingerprint”, also known as a “Checksum” or “Hash”, is a mathematic process that’s akin to magic! It’s a way to tell for certain that a piece of digital evidence has not been tampered with.
Skipping the details, the process is that the investigator simply runs a computer algorithm on a digital evidence item, and the algorithm produces a 32-character string consisting of numbers and letters [technically, a 32-digit hexadecimal number] that is unique to the evidence item but cannot be used to re-create the evidence item itself. So, if you create a hash of, say, Fyodor Dostoyevsky’s War and Peace, and then changed, for example, a comma somewhere to a period, the resulting modified book would produce a hash totally unlike the first one.
Hashes are used all the time in computer forensics to insure the integrity of evidence.
Just as with fingerprints, DNA samples, and other evidence, digital evidence requires a chain of custody to insure the level of integrity demanded by modern legal systems. Just as each of the types of traditional evidence has its own special rules for evidence handling and chain of custody, so does digital evidence.
Unlike traditional evidence, however, it’s often possible to create exact copies of digital evidence, using hashes to insure fidelity. It’s also important to keep digital evidence in an organized file system to avoid confusion.
Also, digital evidence can be corrupted simply by viewing it, since file systems generally change the metadata associated with files and devices. Further, device batteries can die, producing unexpected results when they start up again with new batteries.
Welcome to the wonderful, exciting world of theft of Trade Secrets! While we are NOT attorneys [and we don’t even play them on television], we work with this stuff all the time, and here are our take-aways.
Of the four classes of intellectual property – Patents, Copyrights, Trademarks, and Trade Secrets – only one, Trade Secrets, carries potential criminal penalties for misappropriation [”theft of Trade Secrets”], although that is extremely rare. By far the most common form of Trade Secret theft is the theft of customer lists.
Theft of Trade Secret cases generally require financial analysis in order to determine a fair value for recovery, potentially including unjust enrichment as well as other damages. Our senior staff includes a trained accountant who took a firm public under the rules of the US Securities and Exchange Commission as its CFO.
About Us

Wayne B. Norris
Principal Scientist
Wayne has a broad range of experience in numerous technical and non-technical disciplines.
Wayne has served as an expert witness in more than 110 cases since 1986 in State and Federal courts, including the $1.7 billion Microsoft et al vs Commissioner of Internal Revenue from 1997-99, where he served as the US Government’s chief expert witness in software development.
Prior to spending full time on his expert witness practice, he served as the CEO of Precision Simulations, a forensic video firm, in 2017. He previously served as a cybersecurity manager and project management instructor for the US Navy at Port Hueneme.
From 2005 to 2010 he served as the Chief Scientist for SEDS, LLC, a nuclear research firm developing thermal neutron and gamma ray technologies for detecting hidden non-nuclear and nuclear weapons in theater. During this time he delivered more than 50 invited talks, primarily in the Washington, DC area, to industry, defense, national security, and Congressional and Senate groups and was interviewed regarding counterterrorism on Anderson Cooper 360.
From 2003 to 2005, he served as President and CFO of a 130-person Ukrainian American software company, which he took public before the US Securities and Exchange Commission in 2005.
Wayne holds a BA degree from the University of California in Santa Barbara and is also university trained as an accountant to the standards required for CPA designation, though he has not
completed the certification. He holds certifications as a Project Management Professional, as a US Government Security Manager, and as a Hazardous Materials Operator, from the University of Texas at Austin. He holds an Airline Transport Pilot Certificate from the FAA and is a former Certificated Flight Instructor.

Robert Ayers
Senior Analyst
Robert Ayers, prior to becoming an Expert Witness and joining Norris-Technologies and Associates, was President and CEO of Golden Reflections, Ayers Automotive Repairs, a premiere automotive services business in Santa Barbara, California for 43 years.
As an Expert Witness, Mr. Ayers has completed and is certified as a Magnet DVR Examiner, Magnet Certified Video Examiner. He is also well versed in the use of Magnet Axiom Cyber, Exterro FTK and FTK Imager, Autopsy from the Sleuth Kit, Video Cleaner, and uses Logic Cube – Falcon Neo and Talon Ultimate for forensic imaging, as well as using Cellebrite, plus a multitude of other tools. He continues to keep his technical and business skills current by attending classes at Santa Barbara City College, Coursera, and industry seminars.
Mr. Ayers holds a pilot’s license and the newest in Coast Guard Safe Boaters Certifications for California, Nevada, and Arizona. He has been an avid photographer since his youth. Over the years he has been extremely involved in the training of youth in the community through the Santa Barbara School District Partners in Education Programs. He has also been in active in promoting a positive public image of the independent automotive aftermarket through positions with the Automotive Service Councils of California, Independent Professionals Association, Automotive Service Association, and other community groups.
For additional credentials please see Mr. Ayers’ CV Report.

Nikki Ayers
Senior Analyst
Nikki Ayers, prior to joining Norris-Technologies and Associates, was the CFO of Golden Reflections, Ayers Automotive Repairs, a premier automotive services company in Santa Barbara, California for 43 years. Mrs. Ayers managed the operations and HR aspects of the business.